
I just finished building my new website, and finally have everything just right (well 99% right…for now…you know how that goes). Now it’s time to put in place an effective backup solution. In particular I am looking for a cost-efficient, very reliable, and very secure way to automatically backup my websites and databases once per day. I have Virtualmin GPL running as my control panel at my Linode VPS, so I already have cost-effective and very reliable covered (alternatively, Duplicator Pro is the best WordPress plugin that will do the same thing). Now I just have to make sure it is secured properly, or a server hack could turn into a data breach nightmare.
The thing is if your server ever gets hacked (never assume it won’t be) and you are running automated remote backups, there is a risk of the hacker accessing your remote account where you backup your server to. So any decent setup requires isolating your backup environment from any of your other critical data that may be on that remote account. Who cares if they get that server’s backups if they are already in that server…as long as the buck stops there.
I discovered that there is a way you can allow access to your Amazon S3 Bucket account without risking the security of any data outside a particular bucket. This is good news, because Amazon S3 Bucket is not only very affordable, it’s also very reliable and scalable (holds Gigabytes of data for pennies a month with no limits).
First off we need to sign into IAM (Identity and Access Management) at AWS. Once logged in, first we create a new user:
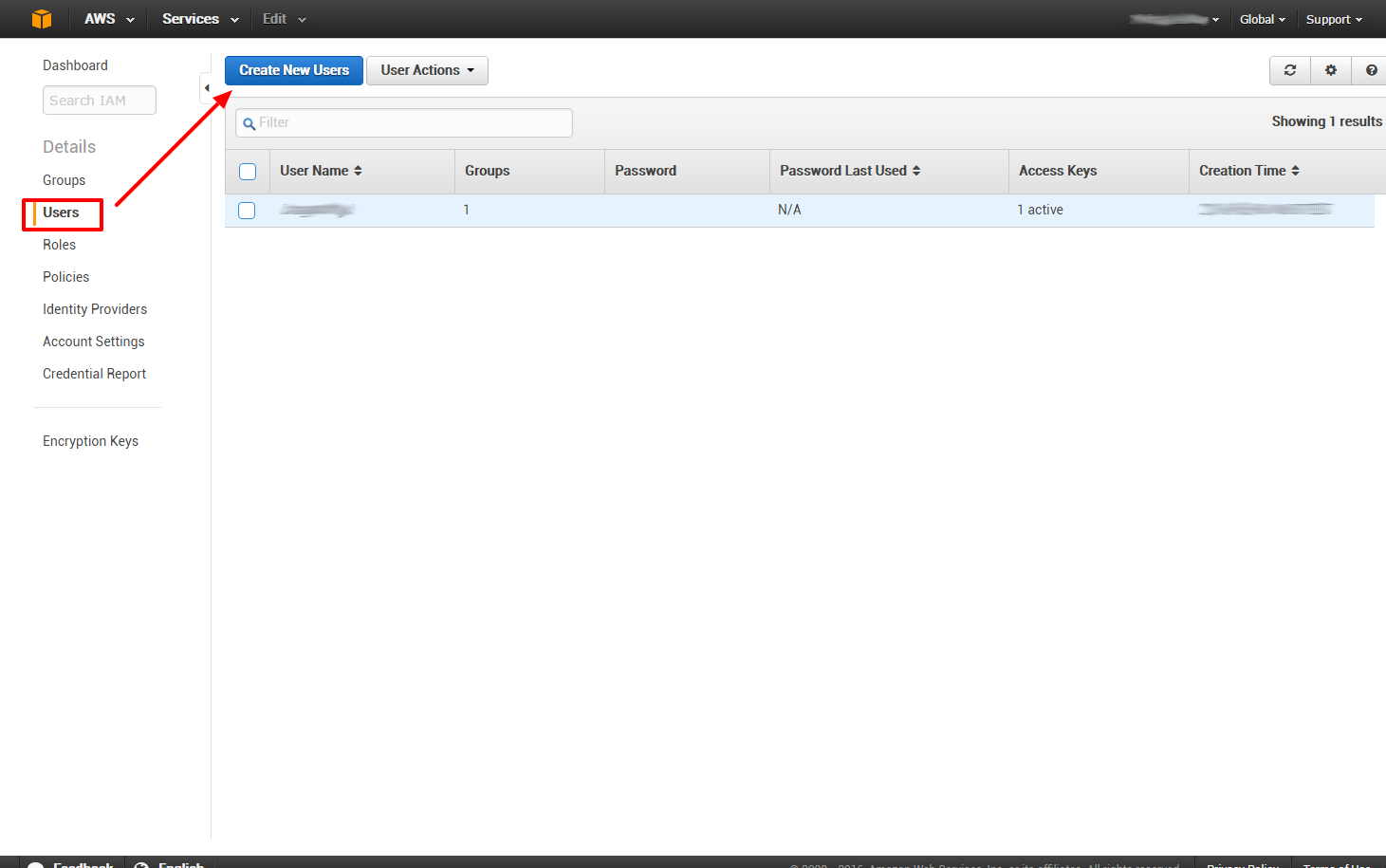
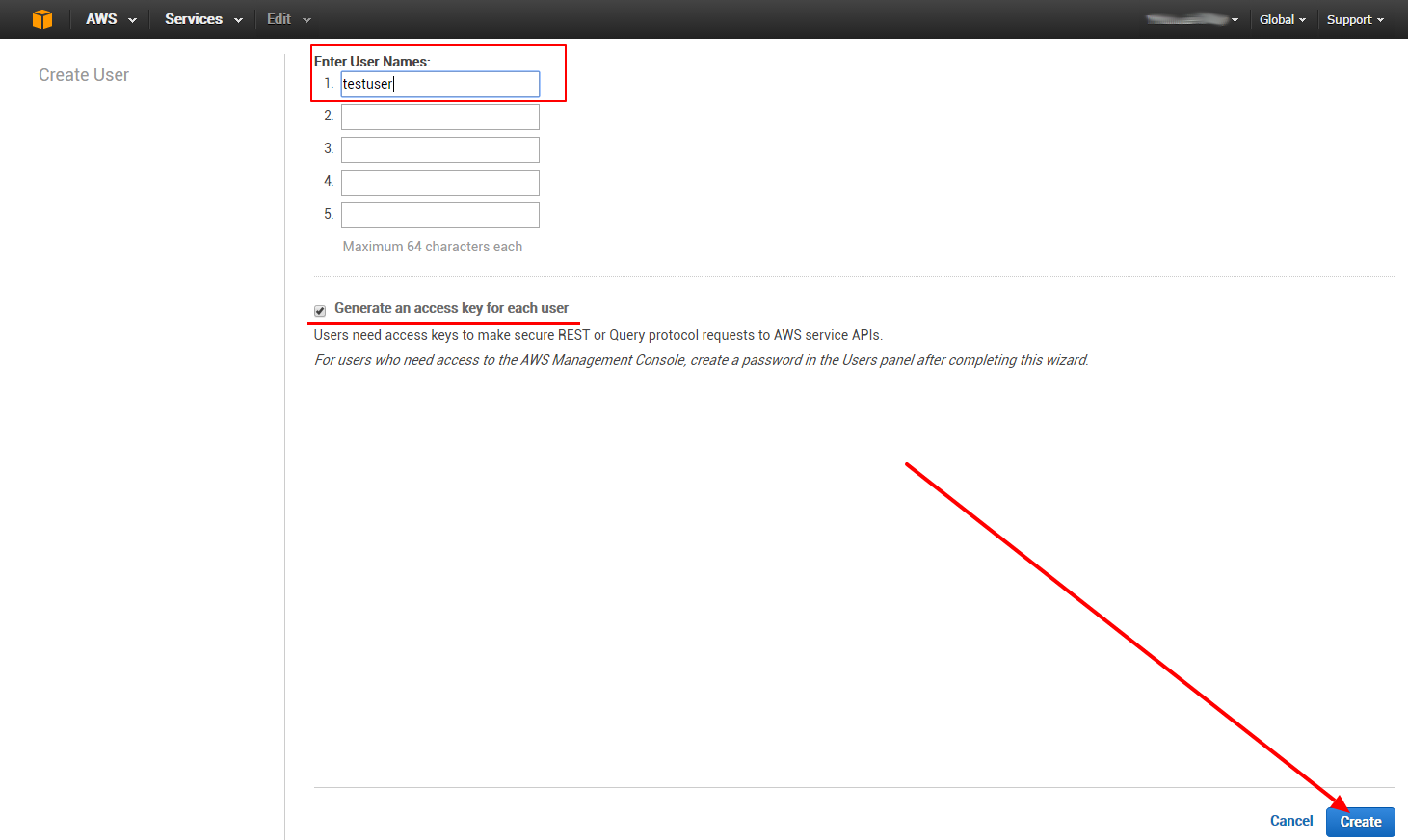
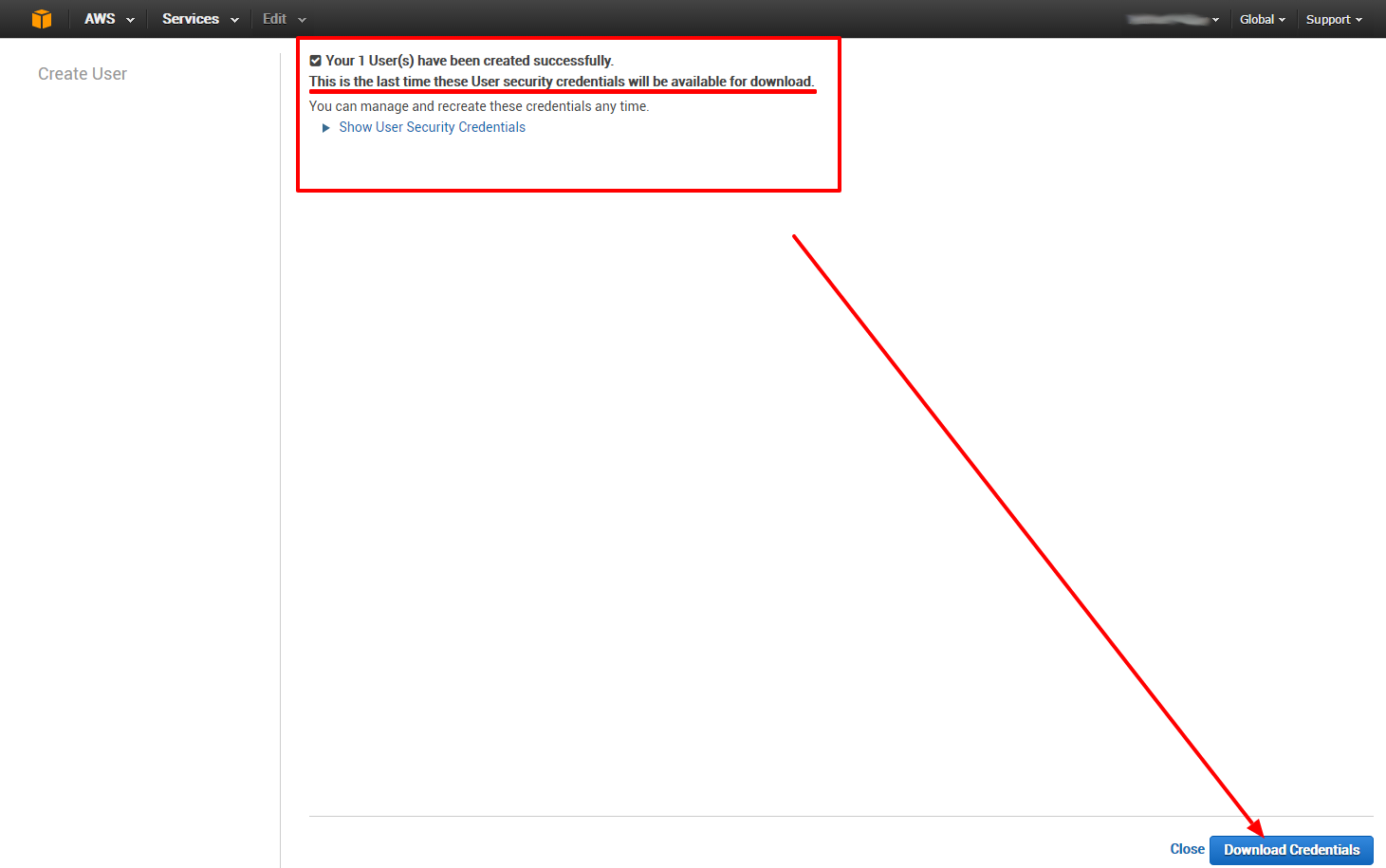
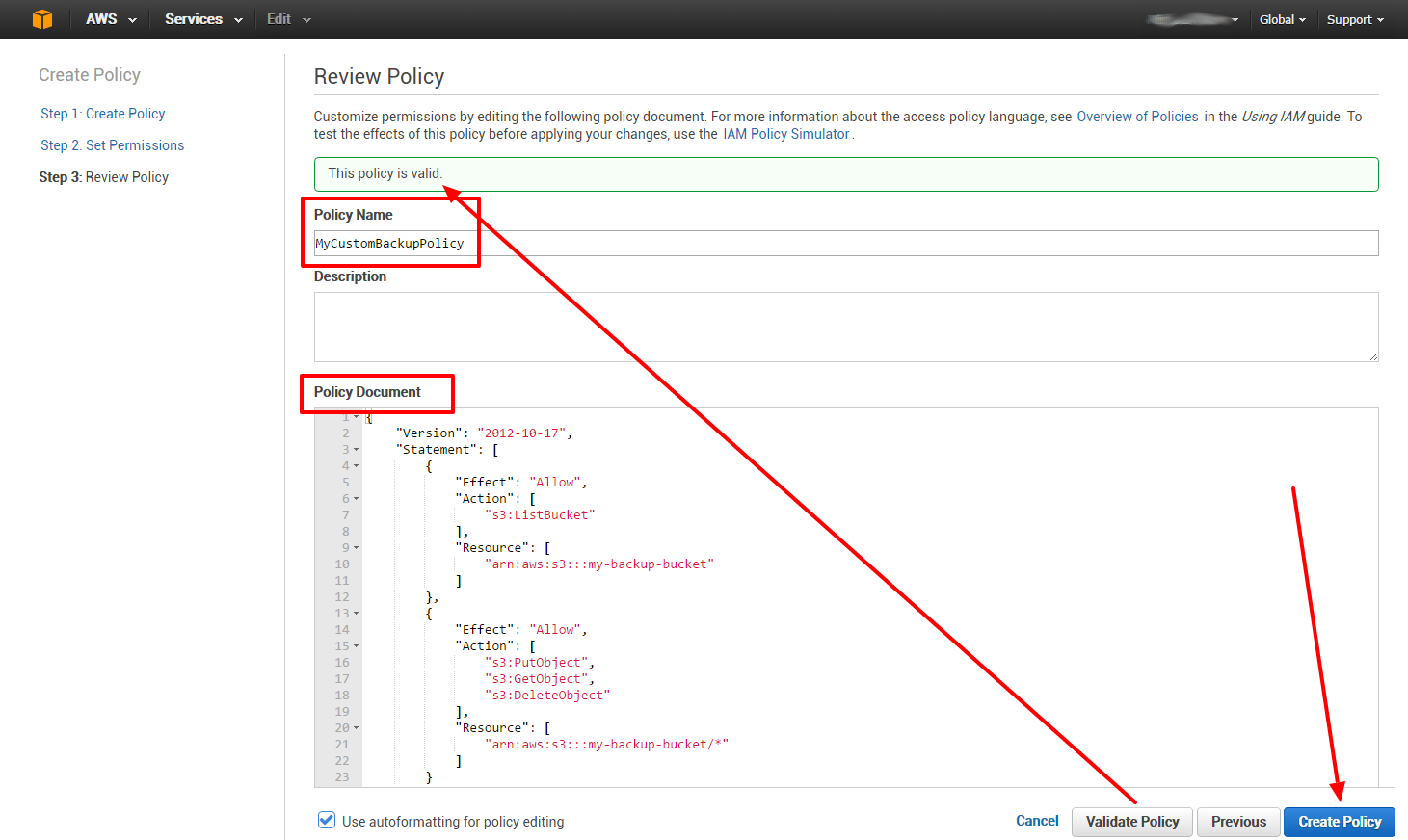
Now we create our custom policy:
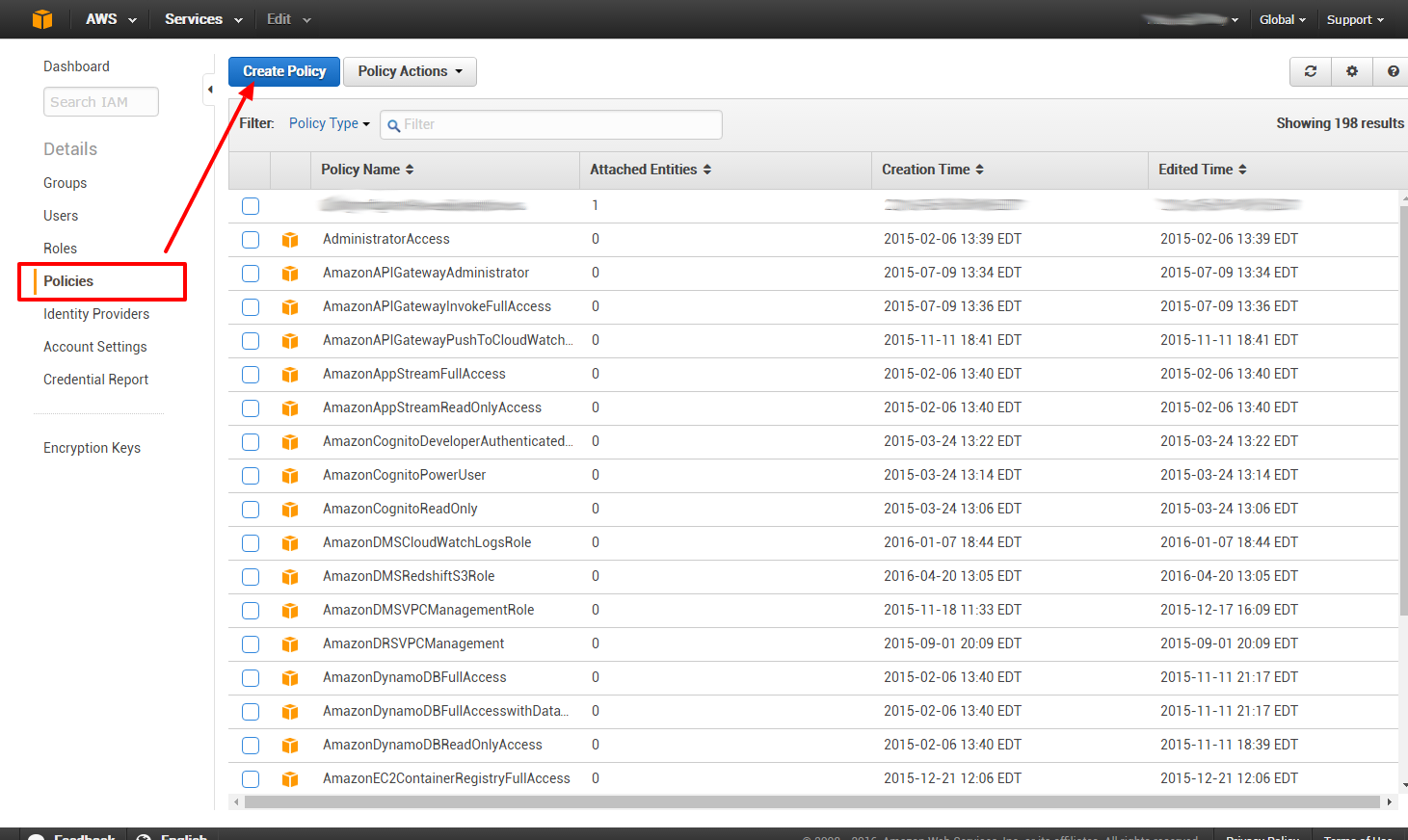
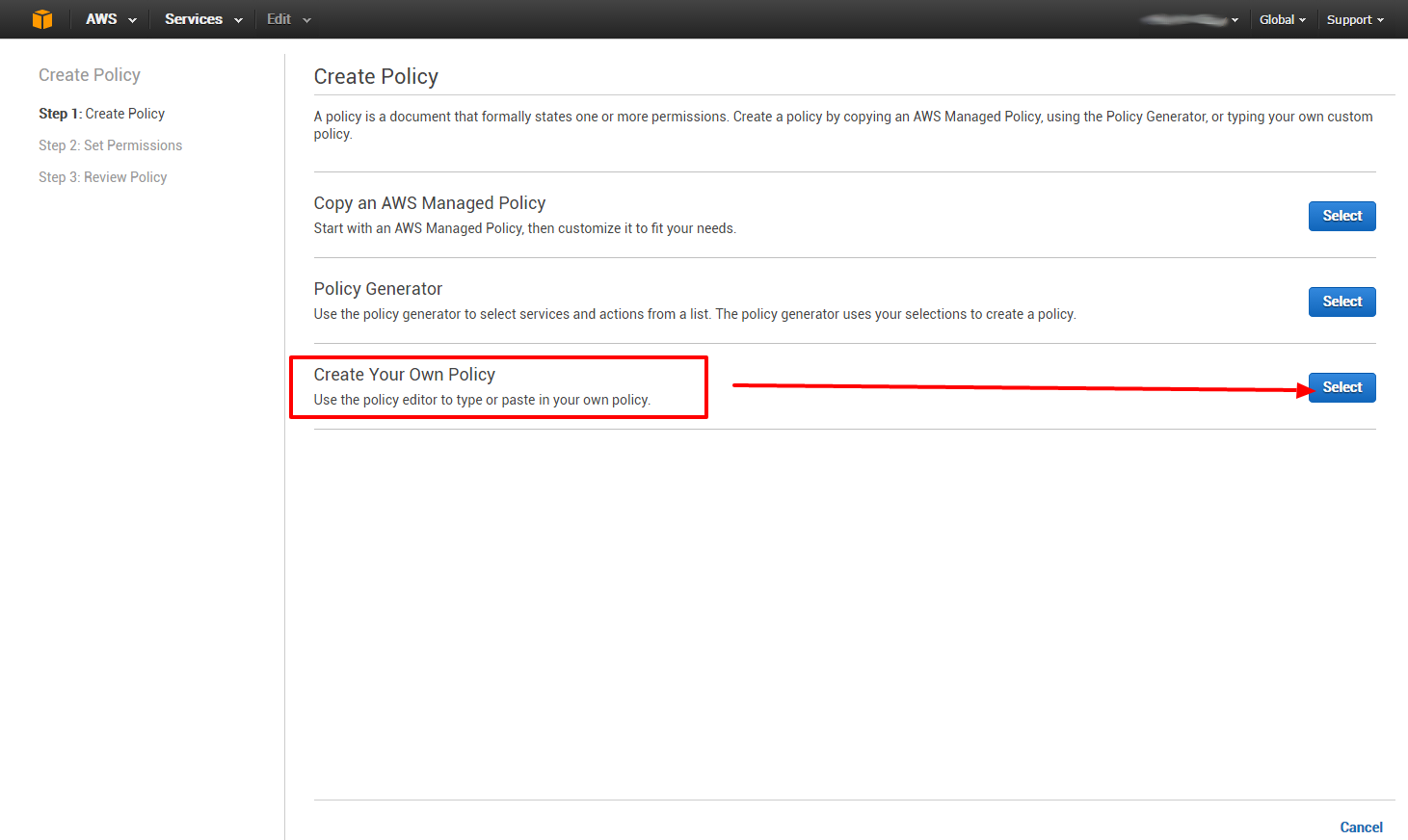
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": ["s3:ListBucket"],
"Resource": ["arn:aws:s3:::my-backup-bucket"]
},
{
"Effect": "Allow",
"Action": [
"s3:PutObject",
"s3:GetObject",
"s3:DeleteObject"
],
"Resource": ["arn:aws:s3:::my-backup-bucket/*"]
}
]
}
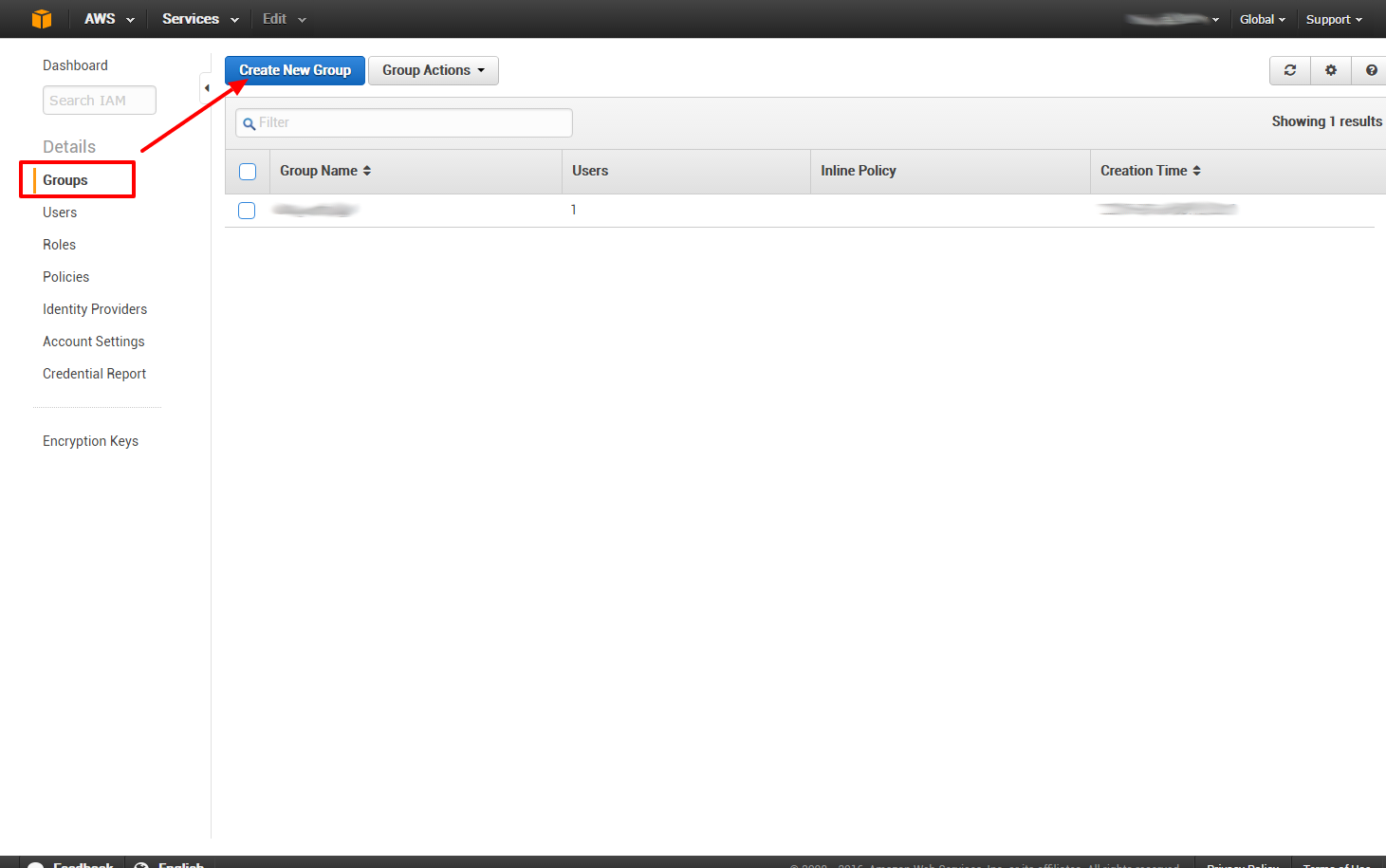
Now we create a group, with the same name as our user for simplicity:
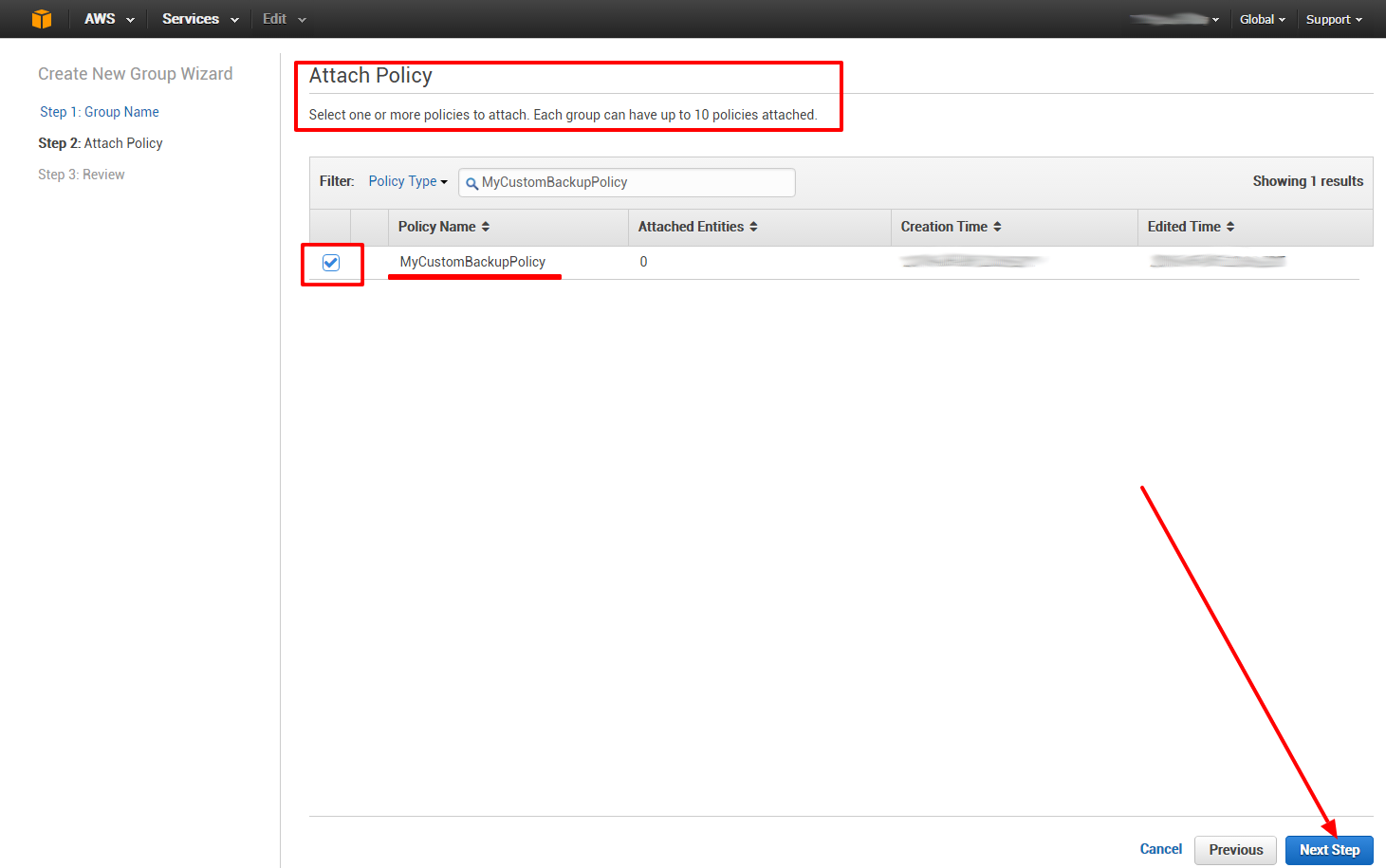
And attach our custom policy to this group:
Make sure the bucket has been created already that you added in the policy code. If not, create it as a full administrator before proceeding any further.
Now you can connect to Amazon S3 Bucket using your access keys you saved earlier for your new user, and use the bucket name you put in the policy code. This user is never allowed out of this bucket in any way, so it is safe to use with your server backup bucket…but only if you stick to using this special user we created for it.


Recent Comments